Shellcode is not specific to a particular processor architecture. – Shellcode is not specific to a particular processor architecture, a characteristic that grants it remarkable portability and adaptability. This architectural independence allows shellcode to execute seamlessly across diverse platforms, making it a formidable tool in the realm of cyberattacks. In this discourse, we delve into the intricacies of shellcode’s architecture independence, exploring its benefits, challenges, and security implications.
The portability of shellcode stems from its ability to leverage common instruction sets that transcend specific processor architectures. This cross-platform compatibility enables attackers to target multiple systems with a single payload, amplifying their reach and impact.
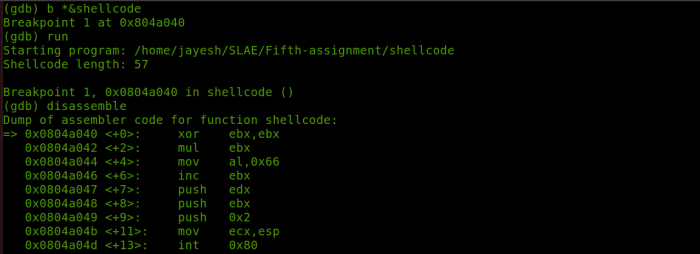
Shellcode Architecture Independence
Shellcode, malicious code that allows attackers to execute arbitrary commands on a compromised system, is not tied to a specific processor architecture. This independence enables attackers to target multiple platforms with a single shellcode payload, making it a potent threat in cross-platform attacks.
Shellcode can be executed on different architectures by exploiting commonalities between instruction sets and system calls. For instance, a shellcode written for x86 architecture can often be executed on x86-64 systems with minimal modifications, as both architectures share similar instruction sets.
Architecture independence offers several benefits for shellcode:
- Increased attack surface: By targeting multiple architectures, attackers can compromise a wider range of systems with a single payload.
- Evasion of detection: Shellcode that is not specific to a particular architecture may evade detection by traditional security measures, such as signature-based antivirus.
- Code reusability: Shellcode can be easily ported to different architectures, reducing the effort required to create custom payloads for each target platform.
Portability and Reusability
Shellcode’s architecture independence allows for easy portability and reusability across different platforms. This portability stems from the use of assembly language, which is relatively independent of the underlying hardware architecture. By using assembly instructions that are common across different architectures, shellcode can be easily ported to new platforms with minimal modifications.
However, porting shellcode to new architectures can present challenges and limitations:
- Instruction set differences: Different architectures have unique instruction sets, which may require modifications to the shellcode to ensure proper execution.
- System call conventions: System calls, which allow shellcode to interact with the operating system, vary across architectures, necessitating changes to the shellcode to accommodate these differences.
- Endianness: The way in which data is stored in memory (little-endian or big-endian) can affect the portability of shellcode, as it may need to be modified to match the target platform’s endianness.
Despite these challenges, shellcode has been successfully ported to various platforms, including Windows, Linux, and macOS, demonstrating its versatility and adaptability.
Set Compatibility
The ability of shellcode to execute on a specific architecture is determined by its compatibility with the target platform’s instruction set and system call conventions. Set compatibility refers to the alignment between the shellcode’s instructions and the target platform’s expected behavior.
To ensure set compatibility, shellcode can be modified to:
- Match the target platform’s instruction set: The shellcode can be rewritten using instructions that are supported by the target architecture.
- Adhere to the target platform’s system call conventions: The shellcode can be modified to use the correct calling conventions for the target platform, ensuring proper interaction with the operating system.
- Handle endianness differences: If the target platform has a different endianness than the platform on which the shellcode was originally written, the shellcode can be modified to handle these differences correctly.
By ensuring set compatibility, shellcode can be executed on the target platform, allowing attackers to gain control of the system and perform malicious actions.
Security Implications
The architecture independence of shellcode poses significant security implications, as it allows attackers to target multiple platforms with a single payload. This can lead to widespread infections and compromise of systems across different architectures.
Attackers can exploit shellcode architecture independence to:
- Target multiple platforms: A single shellcode payload can be used to compromise systems running on different architectures, increasing the attack surface for malicious actors.
- Evade detection: Shellcode that is not specific to a particular architecture may evade detection by traditional security measures, such as signature-based antivirus, as it does not match known attack patterns.
- Increase the impact of attacks: By targeting multiple platforms, attackers can amplify the impact of their attacks, potentially compromising a large number of systems and causing significant damage.
Real-world attacks have demonstrated the effectiveness of shellcode architecture independence. For example, the Stuxnet worm, which targeted industrial control systems, used shellcode that was designed to execute on multiple architectures, allowing it to infect a wide range of systems.
Countermeasures and Mitigation Techniques, Shellcode is not specific to a particular processor architecture.
To protect against architecture-independent shellcode attacks, several countermeasures and mitigation techniques can be implemented:
- Instruction set randomization: This technique involves randomizing the instruction set of the target platform, making it more difficult for shellcode to execute properly.
- Control flow integrity: This technique ensures that the flow of execution follows a predefined path, preventing attackers from executing arbitrary code.
- Memory protection: This technique involves protecting memory regions from unauthorized access and execution, preventing shellcode from being injected into memory and executed.
- Signature-based detection: While traditional signature-based detection may not be effective against architecture-independent shellcode, advanced detection techniques can be employed to identify and block malicious payloads based on their behavior and patterns.
These countermeasures can be effective in mitigating architecture-independent shellcode attacks, but they also have their limitations and can be bypassed by sophisticated attackers. Developing effective countermeasures against shellcode architecture independence remains an ongoing challenge for security researchers.
FAQ Guide: Shellcode Is Not Specific To A Particular Processor Architecture.
What are the key benefits of shellcode’s architectural independence?
Shellcode’s architectural independence offers several advantages, including increased portability, reusability, and the ability to target multiple platforms with a single payload.
How can attackers exploit shellcode’s architectural independence?
Attackers can leverage shellcode’s architectural independence to launch cross-platform attacks, targeting a wider range of systems and increasing the impact of their malicious activities.
What are some effective countermeasures against architecture-independent shellcode attacks?
Effective countermeasures against architecture-independent shellcode attacks include code signing, memory protection techniques, and the use of intrusion detection and prevention systems.